In total, around $3 billion worth of crypto-assets were stolen in 2020. These kinds of theft can happen for many reasons and the biggest one is coming from users themselves. When it comes to using a proper email address, to set up a strong password or to enable the 2FA authentication, these elements sometimes lead to weaknesses and thus, a workable breach for hackers. Choosing the most suitable security to your needs is the key to protect yourself from attacks. Encrypted wallets may be the solution.
Before choosing how you want to secure your cryptocurrencies, you might want to understand how a wallet works and what happens when you send and receive cryptocurrencies. In this article, we will take a look at the technology powering wallets, public and private keys. The basic principle of cryptography relies on blockchain technology, we deal in another article what is blockchain.
The vast majority of digital wallets are softwares interacting with the blockchain, or even multiple blockchains. The same way paper wallets store your public and private keys, a digital wallet saves them and accesses all of your digital ledgers at once. While you might think cryptocurrencies are stored on the wallet itself, the fact is that it is not. Indeed, all a wallet can do is secure your access points to the blockchain. But to understand deeper how a wallet is interacting with you and the blockchain, we must dive deeper into the definitions of cryptography, public keys and private keys.
Cryptography : a brief history
Public key cryptography is an asymmetric encryption system allowing to validate the authenticity of something. First used in the military to send secret messages, asymmetric encryption improved over time to become one of the best ways to ensure high level security of information. The first use of coded encryption dates back to the Roman empire. Officers would write a message on a leather band and could only be read if the receiver had a stick with the good dimensions to wrap it around. The first symmetrical encryption system was born, along with its flaws : anyone with the right stick could break the secret.
During the 13th century, for the purposes of securing communications and protecting pilgrim capital, Templars developed the block cipher system. Provided that both the sender and receiver had the same key, the ciphers could encrypt and decrypt the message. The last great example of cryptography is the enigma encryption cipher. Mostly known to be used by the wehrmacht during world war two, it is one of the first machines to use polyalphabetic encryption, where each press of a button changed the alphabet. Unfortunately for its users, the cryptographic algorithm wasn’t safer (just longer) than in the 13th century and once the public key encryption was broken, any encrypted message could be read.
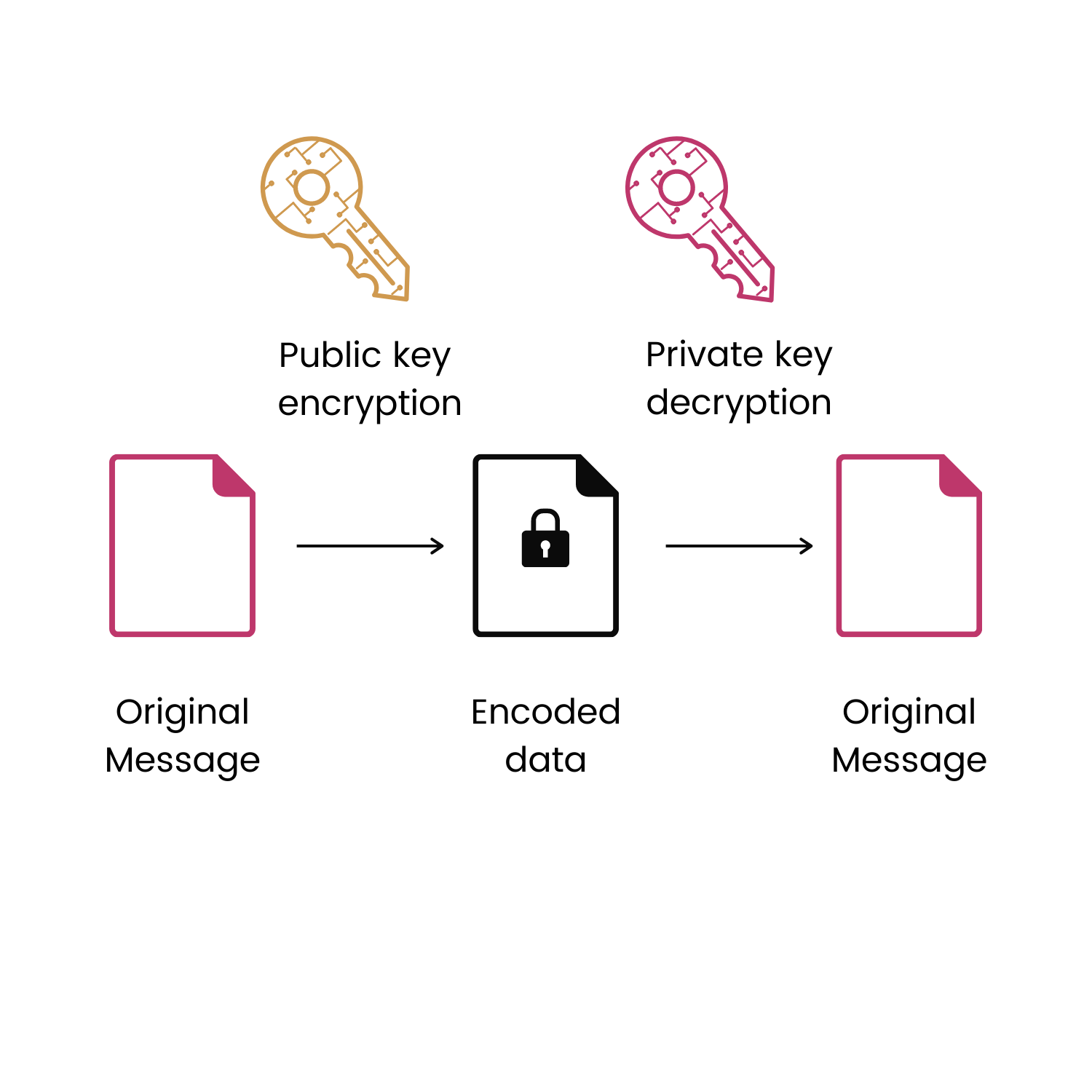
Public key cryptography is used now in cryptocurrencies to authenticate a transaction and to confirm its registration into the blockchain. Simply explained, it is a one way mathematical equation that can be easily solved if you have the right answer and tremendously hard if you try to break it without it. It is not “unbreakable” so to speak, but it is humanly impossible to outlive the time between the moment you begin to hack the equation and the moment you solve it. It would take hundreds of years, even with a supercomputer. Public Key Encryption takes a step further in cryptography by using public keys and introducing private keys.
Public Keys
Whenever you generate a wallet on the blockchain, either by doing it yourself or buying a device with pre-integrated public and private keys, you have what is called a public address. This address is your pseudonym on the blockchain anyone can send cryptocurrencies to. Your public address is the shortened version of your public key making it easier to be shared. To access the public address you need the private key, so as long as nobody else knows your private key, you can freely share your public address.
Private Keys
Private keys can take many forms and allow you to access your public address, and so make transfers and sign off on transactions. As their name suggests, you should never share them with anyone. Remaining private and well secured, they are the last line of defense against, say a hack of your wallet device. Private keys can take many forms like a long binary code, its shorter version in hexadecimal, a Qrcode or even a mnemonic sentence. It doesn’t matter the form as long as you store it properly in a place away from prying eyes.
How a wallet interacts with you and the blockchain
Now that you know the difference between public and private keys, it is important to address the question of how they interact with each other, with you, and with the blockchain.
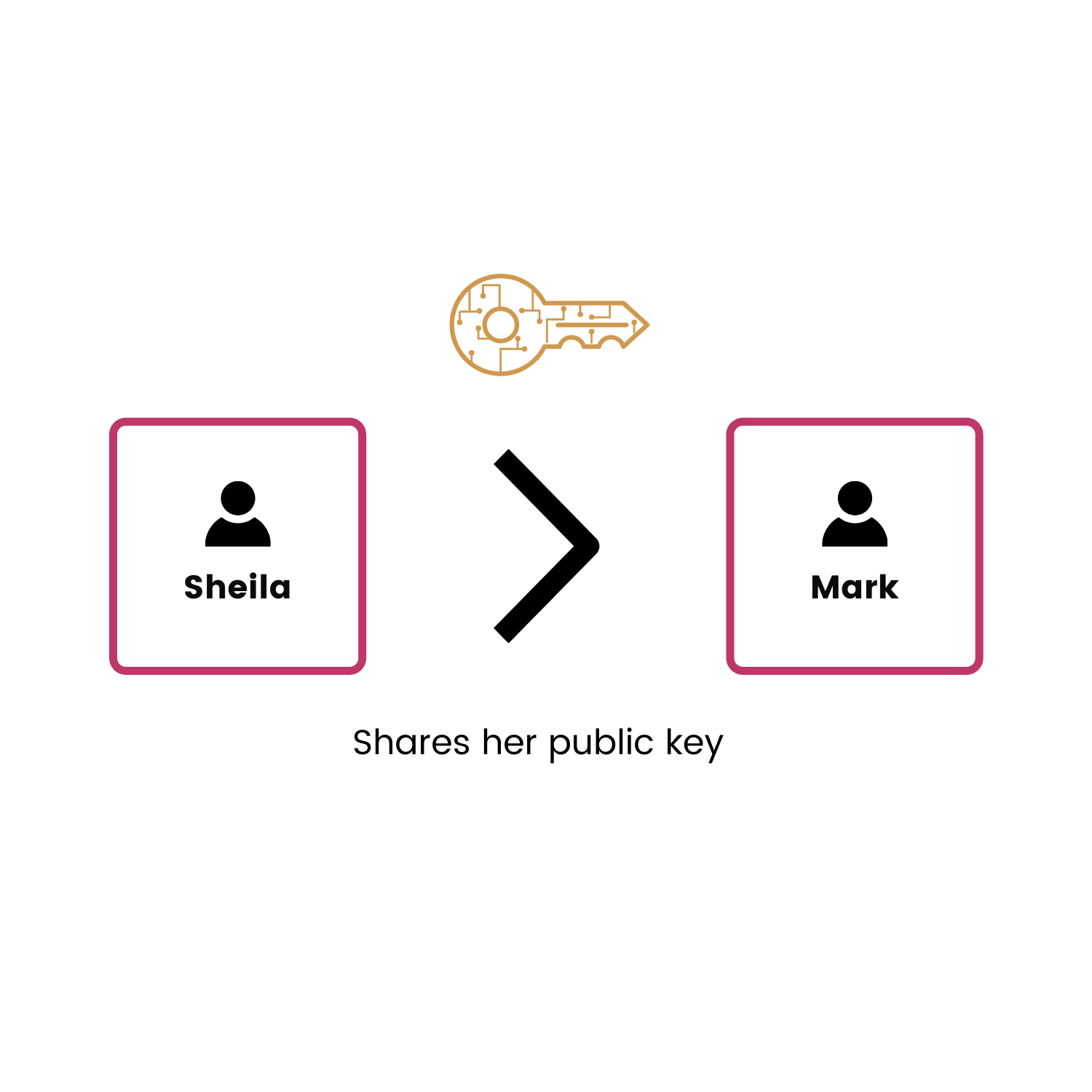
Let’s say, Mark wants to send 1 BTC to her friend Sheila.
The first thing Mark needs to do is to access his wallet. He will take his private key and enter it on his login interface to retrieve his funds. Once connected he will be able to see his public address. In order for Mark to send the BTC to Sheila, she will send him her public address after proceeding with the same authentication process on her account.
After that Mark sets the amount of BTC he wants to send and the public address of Sheila, and starts the transfer process. Here’s where it is getting interesting ! What happens at that moment ?
First the transaction information is encrypted automatically by Mark’s private key, signing digitally that he is the sole person at the origin of the transfer. Once encrypted, the transaction is sent on the blockchain, which verifies the content and authenticity of the information. Once the blockchain approves the transaction Sheila’s private key decrypts the transaction information and adjusts her BTC balance by +1.
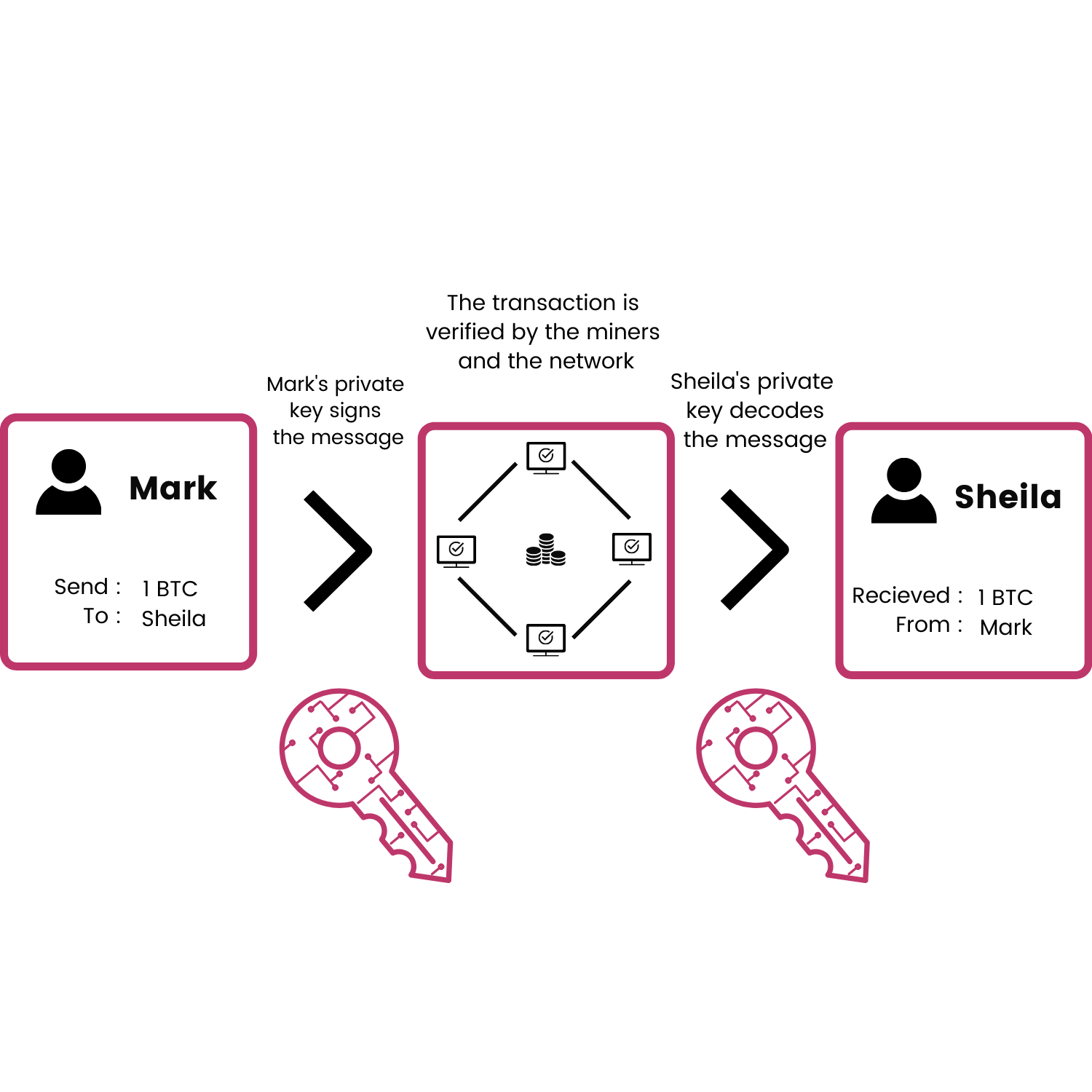
Basically the Bitcoin blockchain verifies the authenticity of the transaction by a proof-of-work system, allowing to ensure the authenticity of all the transactions and a register impossible to hack.